Sunday, June 21, 2009
Unable To See Hidden Files...???
Saturday, June 20, 2009
Firefox v/s Chrome...!!!

Google claims that V8, an open source Javascript engine, which is heart of Chrome, is faster than anything currently offered on the Web.
Thursday, June 18, 2009
How does Computer Worms work ???

Worms can spread rapidly over computer networks, the traffic they create bringing those networks to a crawl. And worms can cause other damage, such as allowing unauthorized access to a computer network, or deleting or copying files.
So what exactly is a computer worm???
Wednesday, June 17, 2009
Spyware – A Threat To Your Privacy -->>INFO and DEFENCE...???
Microsoft’s WorldWide Telescope: Virtual telescope opens night sky...!!!
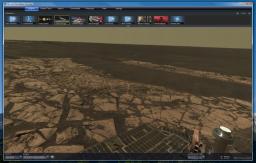 Joining Google Sky and Stellarium is Microsoft’s entrant to the stars, Worldwide Telescope. I’ve been playing around with it for about an hour and it’s pretty cool. It effectively turns every computer that downloads it into a mini-planetarium capable of displaying high resolution images of millions of stars, planets and other celestial.
Joining Google Sky and Stellarium is Microsoft’s entrant to the stars, Worldwide Telescope. I’ve been playing around with it for about an hour and it’s pretty cool. It effectively turns every computer that downloads it into a mini-planetarium capable of displaying high resolution images of millions of stars, planets and other celestial.Semantic E-mail Delivery: The Future of E-mail?
Smart email figures out who should get messages...!!!
--> New cutting edge technology? or just another waste of time? Perhaps you might discover a life-changing potential so stay tuned.
A prototype e-mail system being tested at Stanford University later this year will radically change how users specify where their messages are supposed to be delivered. Called SEAmail, for “semantic e-mail addressing,” the system allows users to direct a message to people who fulfill certain criteria without necessarily knowing recipients’ e-mail addresses, or even their names. In SEAmail, a user selects recipients for a message in much the way that he would set up a search query. The parameters can be as simple as a person’s name, or as complex as sets of logical requirements.
In SEAmail, a user selects recipients for a message in much the way that he would set up a search query. The parameters can be as simple as a person’s name, or as complex as sets of logical requirements.
Yes, a user could also send a message to a group such as “say … all girls who graduated from Xyz School in 2000″ ![]() or I can see it working within companies i.e. “email all people working on SSAS.” SEAmail can handle that without requiring the user to spend time doing research or keeping an address book up to date.
or I can see it working within companies i.e. “email all people working on SSAS.” SEAmail can handle that without requiring the user to spend time doing research or keeping an address book up to date.
But the system is limited by how much information it has about potential recipients. Within an organization, there’s usually a lot of available data. The technical challenge is setting up an integrated version of the data that SEAmail can access easily.
First thing that came to my mind about this technology is “spammer’s heaven” ![]() . You can target the exact group of people without even knowing their email IDs, bringing accuracy to junk. Is it ripe for misuse? Will there be more time spent patching than progressing? On first look, “Yes”.
. You can target the exact group of people without even knowing their email IDs, bringing accuracy to junk. Is it ripe for misuse? Will there be more time spent patching than progressing? On first look, “Yes”.
Assuming that worries about spam could be properly resolved, still getting good data for SEAmail becomes a much harder problem on the broader Internet.
Also outdated information could degrade the quality of the system.
Still I think there is a lot of potential for internal use by large businesses, for which its benefits far outweigh the potential for abuse.
Even with issues, more of social than technological, SEAmail is ready to impact the way we mail and this may be something you’ll hear more about....!!!
Semantic E-mail Delivery: The Future of E-mail?
Smart email figures out who should get messages...!!!
--> New cutting edge technology? or just another waste of time? Perhaps you might discover a life-changing potential so stay tuned.
A prototype e-mail system being tested at Stanford University later this year will radically change how users specify where their messages are supposed to be delivered. Called SEAmail, for “semantic e-mail addressing,” the system allows users to direct a message to people who fulfill certain criteria without necessarily knowing recipients’ e-mail addresses, or even their names. In SEAmail, a user selects recipients for a message in much the way that he would set up a search query. The parameters can be as simple as a person’s name, or as complex as sets of logical requirements.
In SEAmail, a user selects recipients for a message in much the way that he would set up a search query. The parameters can be as simple as a person’s name, or as complex as sets of logical requirements.
Yes, a user could also send a message to a group such as “say … all girls who graduated from Xyz School in 2000″ ![]() or I can see it working within companies i.e. “email all people working on SSAS.” SEAmail can handle that without requiring the user to spend time doing research or keeping an address book up to date.
or I can see it working within companies i.e. “email all people working on SSAS.” SEAmail can handle that without requiring the user to spend time doing research or keeping an address book up to date.
But the system is limited by how much information it has about potential recipients. Within an organization, there’s usually a lot of available data. The technical challenge is setting up an integrated version of the data that SEAmail can access easily.
First thing that came to my mind about this technology is “spammer’s heaven” ![]() . You can target the exact group of people without even knowing their email IDs, bringing accuracy to junk. Is it ripe for misuse? Will there be more time spent patching than progressing? On first look, “Yes”.
. You can target the exact group of people without even knowing their email IDs, bringing accuracy to junk. Is it ripe for misuse? Will there be more time spent patching than progressing? On first look, “Yes”.
Assuming that worries about spam could be properly resolved, still getting good data for SEAmail becomes a much harder problem on the broader Internet.
Also outdated information could degrade the quality of the system.
Still I think there is a lot of potential for internal use by large businesses, for which its benefits far outweigh the potential for abuse.
Even with issues, more of social than technological, SEAmail is ready to impact the way we mail and this may be something you’ll hear more about....!!!
Get rid of Windows Vista Administrative Password

Method 1: System Restore
This only works in cases where you changed your password to something new and then forgot it or deleted a user account by accident. In order for this to work, there must be a System Restore point at which a logon was successful for the problem account. Also, this is not a problem if you are in a domain environment because the Domain Administrator can always reset your password.
1. The first thing you’ll need to do is make sure you have your Windows Vista DVD or a repair disc. Insert the disc and then restart the computer. When asked to “Press any key to boot from CD or DVD”, go ahead and press any key.
2. Click Next until you get to the screen that has the option “Repair your computer”, select the operating system you want to repair and then click Next.
N.B. Before reaching this screen, you may have to set preferences for the language to install, time and currency format, and the keyboard or input method.
3. In the System Recovery Options dialog, choose System Restore from the list and then click Next.
4. Now you need to choose the system restore from the list. You want to choose a restore point that will return the computer to a state where the logon was successful and that was using the old password.
5. Then click Next to confirm the disks, then Finish to confirm the restore point and finally Yes in the warning window to begin the restore.
6. Important Note: After you use the System Restore feature, you have to reinstall any programs or updates that were done on the system after that restore point. You will not lose any personal documents; however, you may have to reinstall programs. You might also have to reset some personal settings.
7. When the restore is complete, click on Restart to restart the computer. Click Close to confirm that the restore was successful.
8. You can now try to logon using the older password (in the case where you had reset a password on an user account and then forgot it) or using the normal password (in the case where the account was deleted by accident).
9. If you have simply forgotten your password or cleared the restore point, then this method will not work.
Method 2 : Using NT password and Registry Editor
You need to burn a disk with a special utility called an Offline NT Password and Registry Editor. Here is a link: http://home.eunet.no/pnordahl/ntpasswd/
To use this:
1. Get the machine to boot from CD (or floppy)
2. Floppy version need to swap floppy to load drivers.
3. Load drivers (usually automatic, but possible to run manual select)
4. Disk select; tell which disk contains the Windows system. Optionally you will have to load drivers.
5. PATH select, where on the disk is the system?
6. File select, which parts of registry to load, based on what you want to do.
7. Password reset or other registry edit.
8. Write back to disk (you will be asked)
N.B. The most common problem is that the computer was not cleanly shut down, and the disk won’t write correctly back. (it says: read only file system). If so, boot into Windows Safe Mode (F8 before windows logo appears) and shut down from the login window. You may have to do that twice in a row.
Method 3: ophcrack live cd method
You have to download a CD image from here for this
http://ophcrack.sourceforge.net/
1. Click the button corresponding to the operating system of the computer you’ll be recovering the password on.
2. If you’ve forgotten the password on a Windows XP computer, click on ophcrack XP LiveCD. If you’ve forgotten the password on a Windows Vista computer, click on ophcrack Vista LiveCD.
3. Burn the image into a cd.
4. Insert the Ophcrack Live CD disc into your CD/DVD drive and restart your computer.
5. The initial screen you see after restarting should be the same one you always see immediately after starting your computer. There may be computer information like in this screenshot or there may be a computer manufacturer logo.
6. You don’t need to do anything here. Ophcrack LiveCD will continue automatically after the Automatic boot in x seconds… timer at the bottom of the screen expires. If you’d like to advance the process a little faster, feel free to hit Enter while Ophcrack Graphic mode is highlighted.
7. The next step in the Ophcrack LiveCD boot process is this little window that appears on screen. It may appear and disappear very quickly so you could miss it, but I wanted to point it out because it will be a window that runs in the background that you may see.
8. This message is simply confirming that a partition with encrypted password information on it has been found on your hard drive.
9. The next screen is the Ophcrack LiveCD software itself. Ophcrack will attempt to recover the passwords for all of the user accounts that it can find on your computer. This password cracking process is completely automated.
10. As you can see in the example above, the passwords for the Administrator and Guest accounts are listed as empty. If you were cracking a password for a user that Ophcrack shows as empty, you now know that you can log on to the account without a password at all.
11. Look at the bottom of the list – see the Stacy user account? In under one minute, Ophcrack recovered the password to this account – applesauce. You can ignore any other accounts you’re not interested in recovering the passwords for.
12. After Ophcrack recovers your password, write it down, remove the Ophcrack LiveCD disc from your optical drive and restart your computer. You don’t need to exit the Ophcrack software – it won’t harm your computer to power it off or restart it while it’s running.
N.B. Remember it can only recover password which are up to 14 characters long and do not have any special character (Like @,# etc.) in it.
njoy hacking...!!!